From Ink to Click: How Digital Platforms Redefine Financial Risks
Written by Siby Christopher
TLDR
Global Evolution of Scams: Scams have transitioned from local, face-to-face deceptions to global digital frauds, exploiting anonymity and regulatory loopholes.
Opaque Digital Agreements: “Click-to-accept” terms reduce transparency, limiting user control and amplifying risks.
Cyber Literacy Gaps: Low cyber literacy exposes users to hidden dangers, echoing historical vulnerabilities from literacy gaps.
Collaborative Solutions Needed: Regulators, institutions, and users must unite to balance digital convenience with robust security.
Defending Consumer Trust: Evolving defenses and informed digital engagement are essential to secure a hyperconnected financial world.
Evolution of Scams: A Comparative Analysis across eras
In our previous article, we examined how digital platforms have transformed finance, offering unprecedented speed and accessibility but also creating new vulnerabilities. The modern digital landscape, marked by instant global reach and hyperconnectivity, has opened doors not only for legitimate transactions but also for scams that now operate at a scale and sophistication previously unimaginable. As financial systems evolved, so too did the methods of deception, with technology empowering bad actors to reach across borders, hide their identities, and exploit complex, non-transparent contracts.
Throughout history, scams have reflected the technologies and societal structures of their time, and while technology amplifies the scale and complexity of fraud, it isn’t the sole driver. Notable scams like the South Sea Bubble in the 18th century or early Ponzi schemes reveal that human vulnerabilities to greed and deception have always been targets. But today’s digital infrastructure has eliminated many constraints, enabling bad actors to execute frauds from any location, leveraging anonymous identities, and exploiting regulatory inconsistencies across countries.
This article dives into these shifts, comparing key elements across different periods—from localized, face-to-face scams of the early era to the expansive, anonymous digital frauds of today. By understanding the evolution of scams, we gain insights into the modern landscape’s unique blindspots and trade-offs, where convenience and risk coexist, and the urgent need to address these vulnerabilities in our hyperconnected financial world.
Key Parameters Shaping the Evolution of Financial Scams Across Eras
The table below compares how key elements—such as market access, location, identity concealment, contract complexity, and ledger systems—have evolved from the early days of financial scams to today’s hyper connected digital landscape. Each parameter shows how scams have adapted to technological and regulatory shifts over time, with modern fraudsters exploiting global access, anonymity, and complex contracts to expand their reach and sophistication. This comparison highlights the transformation of scams from localized interactions to global operations, reflecting the new challenges and risks posed by today’s digital era.
Why Bad Actors Flourish in the Digital Financial Landscape?
To navigate and study the rise of scams from financial institutions and individual agents, it is crucial to understand the conditions emboldening these bad actors. They engage in misleading and deceptive practices with the sole motive of maximizing profits at the expense of others. Rapid technological developments have played a major role in giving rise to conditions that affect the world in positive and negative ways.
Modern Digital Age Conditions that Institutional and Individual Scamsters Take Advantage of:
Low-Cost Remote operational capabilities
Lack of transparency and complexity in defining User Engagement Terms & Conditions
Regulatory Gaps and Inconsistencies
Global Market Access
Anonymity Factor (Main factor resulting in enhanced cyber-crime activities by individual agents and hacker groups)
Remote Operations of Financial Institutions
Technological advancements have enabled financial institutions to quickly conduct outreach and draw attention to themselves through digital platforms. This enhanced visibility and access to a wider market pose unprecedented challenges for regulators. The rapid and widespread dissemination of scams makes it difficult to nip such schemes in the bud before many victims have been defrauded. By the time regulators catch up, significant damage may already have been done. Regulators need to develop methods and tools to address these issues at the initial stages, preventing scams from gaining traction.
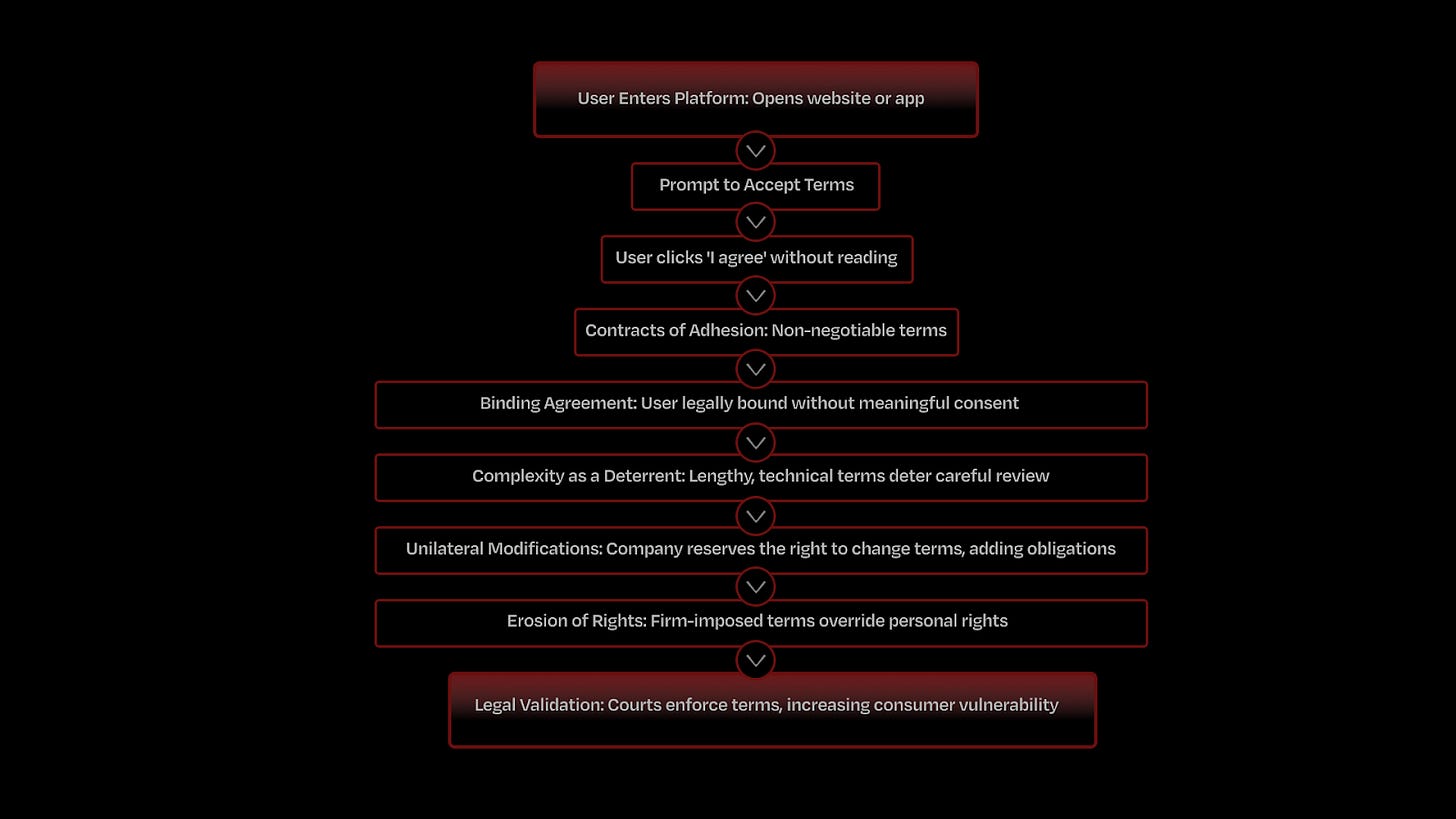
Shoshana Zuboff’s Surveillance Capitalism reveals how the complexity and lack of transparency in digital Terms & Conditions allow companies to operate with minimal user consent. Often labeled as “contracts of adhesion,” these non-negotiable terms force users to accept by simply clicking “I agree,” frequently without reading.
These terms—buried in “click-wrap” or “browse-wrap” agreements—bind users to conditions they seldom understand, creating an “endless loop” of user obligations. The lack of readability is intentional: In 2008, two Carnegie Mellon professors calculated that reading all terms and conditions encountered in a year would require 76 full workdays at a national opportunity cost of $781 billion. The numbers are much higher today. Most users remain unaware of these "rapacious" terms that allow firms "to acquire rights without bargaining and to stealthily establish and embed practices before users, and regulators, realize what has happened," as legal scholar Nancy Kim puts it.
The digital environment exacerbates this issue. Unlike paper contracts, digital agreements are “weightless” and easily expanded, allowing companies to continually adjust terms. Courts uphold these contracts, embedding rights seizures within complex language. Legal scholars like Nancy Kim describe this as “sadistic,” as firms unilaterally gain control, leaving users with few real options.
Evolution of Terms & Conditions: From Offline Paper-Based Contracts to Modern Online Contracts
Below is a comparative table illustrating the evolution of terms & conditions from offline paper-based contracts to modern online contracts, highlighting the limitations that restricted bad actors in the past and the factors that now catalyze their efforts:
Note: While early agreements had natural constraints that limited manipulation, low literacy rates historically made users vulnerable, allowing those with higher literacy, property, or status to exploit these imbalances. Despite this, traditional agreements still permitted some negotiation and customization.
In today’s digital landscape, higher literacy rates haven’t closed these gaps. Instead, bad actors exploit low cyber risk literacy, crafting complex terms to obscure risks. Privacy rights now face the same exploitation that once plagued property rights, with digital agreements enabling unchecked data collection. This shift to standardized “click-to-accept” contracts replaces the flexibility of traditional agreements with a rigid, “take-it-or-leave-it” model, increasing user exposure to hidden risks in an opaque digital system.
Power Imbalances Across Eras: From Literacy Gaps to Cyber Risk Literacy Challenges
In the digital age, these dynamics persist in new forms:
Literacy vs. Cyber Literacy: Historically, low literacy rates allowed those in power to exploit others through written contracts, creating knowledge gaps that disadvantaged the less literate. Today, similarly low levels of cyber literacy expose users to uninformed consent, as complex digital terms are often designed to obscure risks.
Property vs. Privacy Rights: In the past, property rights and written agreements were used as tools to exert control over the less literate. Now, privacy rights face similar threats, as platforms collect user data under opaque “click-to-accept” agreements that obscure the extent of data-sharing practices.
Freedom vs. Privacy/Security Awareness: Traditional contracts allowed for some degree of negotiation, giving individuals more control. Today, however, digital platforms enforce rigid, “take-it-or-leave-it” terms, leaving users with limited awareness and amplifying the risks associated with these non-negotiable agreements.
Conclusion
As we've explored, the transformation from tangible, paper-based transactions to today’s digital engagements has reshaped not only how we interact financially but also the landscape in which scams operate. The digital era, while bringing remarkable convenience and global accessibility, has equally expanded the space for sophisticated fraud. Scams have evolved alongside technology, adapting to and exploiting the blind spots inherent in a hyperconnected world. Today’s challenges stem not merely from technological advances but from widening gaps in user awareness, negotiation power, and control over data privacy—gaps that scams readily exploit.
The shift to a digital-first economy means that money has become increasingly abstract, and so have the risks associated with it. Complex “click-to-accept” terms and conditions obscure transparency, converting user flexibility into rigidity and creating agreements that often prioritize the interests of digital platforms, removing users' negotiation power. This growing power imbalance, combined with the limited regulatory oversight across global digital markets, has left consumers vulnerable to a new generation of scams that operate seamlessly across borders and jurisdictions.
Addressing these vulnerabilities demands more than isolated efforts. It calls for an integrated approach where all stakeholders—regulators, financial institutions, technology providers, and users—work together to balance digital convenience with financial security.
References
Zuboff, S. (2019). The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power. PublicAffairs.
Basel Committee on Banking Supervision (2023). Digital Fraud and Banking: Supervisory and Financial Stability Implications. Bank for International Settlements
Doerr, S., Frost, J., Gambacorta, L., & Shreeti, V. (2023). Big techs in finance. BIS Working Papers No. WP1129. Monetary and Economic Department, Bank for International Settlements.
All artworks are designed by Yosha Waghela.
If you enjoyed reading this blog and would like to receive more such articles from Scaling Trust, please subscribe our blog using the below link:
Alternatively, know more about us on our website here.
Keep in touch with us on: Linkedin | X | Telegram | Youtube | Email