Data in Your Hands: Why Verifiable Credentials Are the Future of Trust
This blog explains how verifiable credentials give people control over their own data; making it portable, trusted, and easy to share across systems.
Every morning in the bustling city of Lagos, Nigeria, Maria sets up her food cart near a busy bus terminal. She serves puff-puffs and jollof rice to a steady stream of commuters, schoolchildren, and workers. What started as a side hustle has grown into her primary livelihood. Now, she wants to invest in better equipment, secure a stall in the market, and eventually hire someone to help.
But when Maria applies for a small business loan at a commercial bank, she is denied. Not for lack of income or discipline, but because the system can’t assess her creditworthiness. She uses mobile money apps like Paga1 and OPay2, logs daily sales by hand, and saves through an ajo3, a rotating savings and credit group where members pool money and take turns receiving the pot. Common across Nigeria, ajos serve as trusted financial lifelines in communities where formal access is limited. Maria may also hold a vendor license, pay local taxes, or promote her business on WhatsApp or Facebook. This wealth of alternate data signals reliability but because it lives in disconnected silos, it remains invisible to the systems that determine access to finance.
Maria’s data exists. It indicates she is creditworthy. But the system cannot verify it.
This is the everyday reality for millions of self-employed individuals and informal workers across the world. They make transactions, build reputations, and generate valuable records but much of this data is out of their reach. It often stays stuck within the systems of banks, hospitals, schools, or government offices, with each institution keeping its own records that don’t easily connect with others. Even when people can access their own data, it usually comes as PDFs, paper documents, or screenshots formats that are hard to verify or use elsewhere.
The result is a system that relies on institutional control and system-to-system integrations. It is expensive, slow, and inaccessible to many. More importantly, it is not designed with the user in mind.
Verifiable credentials offer a different approach. By shifting control back to individuals, they make data portable, tamper-evident, and independently verifiable without needing the issuing institution to intervene each time. This user-centric design enables data to move with the person, not just the institution, creating the foundation for scalable, trusted access to services. Together, these features support a system that is designed to move with people, not around them.
To understand why this matters, we need to look more closely at what’s broken in the way data is shared today and why a different approach is urgently needed.
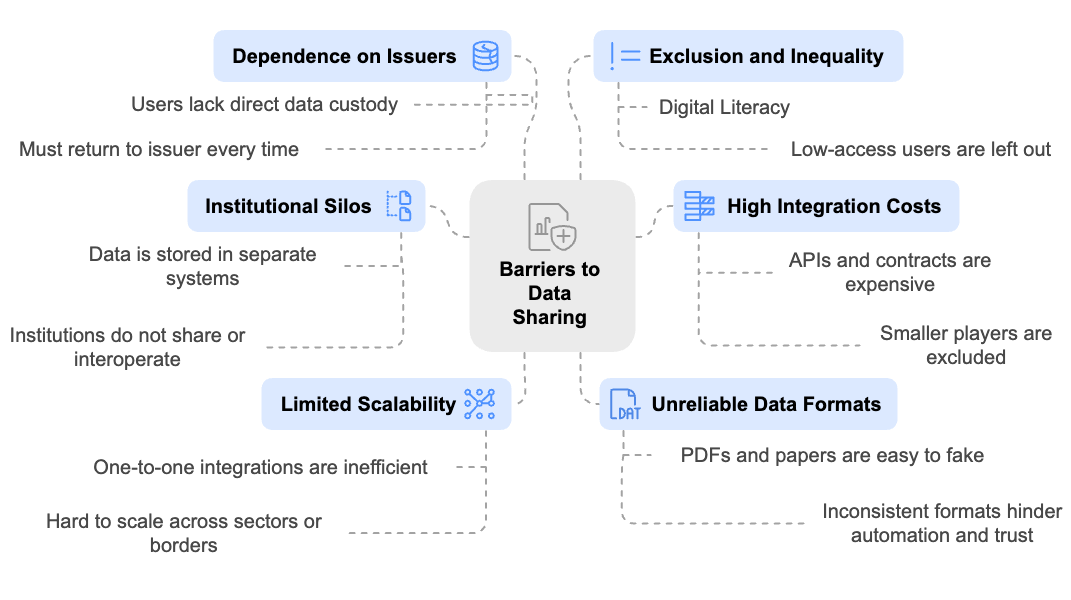
So, Why Can’t the System See the Data People Already Have?
As systems became more digital, institutions began introducing portals and apps to help individuals interact with their data. However, over time, many institutions came to see this data as a competitive asset. To preserve control and maintain an advantage, they made it difficult for others to access the data, even when it rightfully belonged to the user. As a result, institutions rarely coordinate, and the data they hold is often inaccessible to the very individuals it concerns. Even when shared, it typically arrives in formats like PDFs or paper documents that are hard to verify and easy to manipulate. Institutions struggle to trust data they did not generate themselves, which leads to costly verification processes, delays, and frequent exclusion (World Bank, 2021). Sharing data across systems today often requires technical integrations, legal agreements, and real-time infrastructure, which makes the approach too complex and expensive for many smaller institutions (CDPI, 2025).
For users, the result is a high-friction experience. Each time they need to prove their identity, income, or eligibility, they must depend on the issuing institution to validate it again. For instance, even if a user has completed Aadhaar-based eKYC for one financial service, they are often required to repeat the process for another provider due to siloed verification systems and lack of data portability. This leads to repetitive onboarding, delays, and frustration, especially for low-income users or those in remote areas (UIDAI, 2023; RBI, 2022).
The system is not designed for portability or user control. People who have the data still find themselves unable to use it because it cannot be trusted, transferred, or verified at scale.
From the institution’s side, this fragmentation creates barriers too. Banks, government agencies, and service providers may want to support people like Maria but without timely, trustworthy, and interoperable data, they struggle to assess eligibility, verify claims, or onboard new users efficiently. The lack of shared, verifiable records means higher costs, more paperwork, and missed opportunities to serve deserving individuals.
Source: Synthesized from Centre for Digital Public Infrastructure (2025) and World Bank ID4D (2023) insights.
How Verifiable Credentials Shift Control to the User?
Verifiable Credentials (VCs) enable individuals to hold and share tamper-proof, machine-readable data across contexts instantly, securely, and at scale. By making data portable (usable across different platforms and services), verifiable (easily authenticated by third parties without needing to contact the original issuer), and under user control (stored and managed by the individual, not centralized institutions), they turn fragmented records into trusted assets. And trust is what unlocks access.
So, what are verifiable credentials?
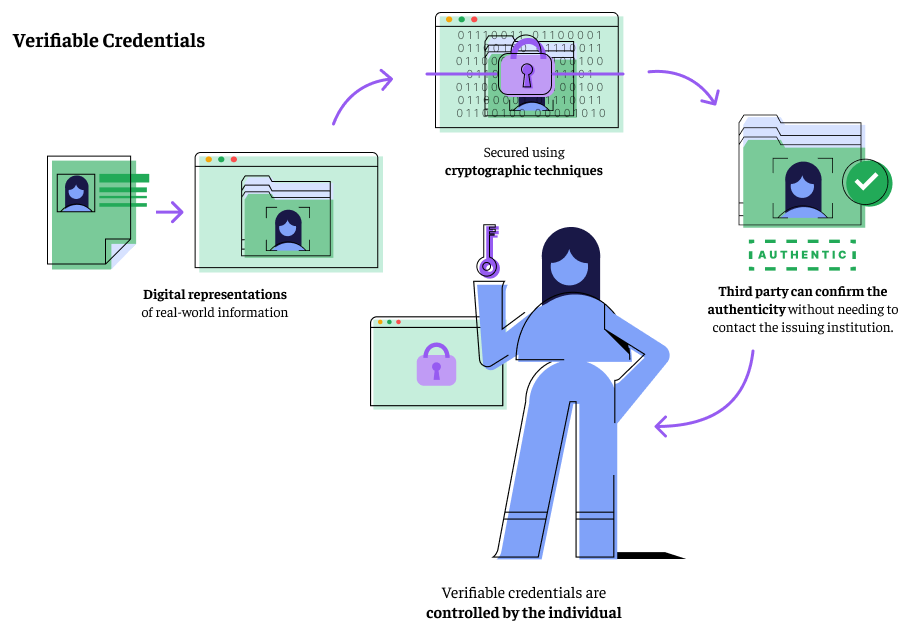
VCs are digital representations of real-world information such as income records, identity documents, academic qualifications, or employment history. Each credential is secured using cryptographic techniques4, which makes it tamper-evident and independently verifiable. This means a third party, like a bank or government agency, can confirm the authenticity of the credential without needing to contact the issuing institution.
Most importantly, verifiable credentials are controlled by the individual. Users can store them in a digital wallet and decide when, where, and with whom to share their data. This user-centric model ensures that trust no longer needs to be rebuilt from scratch each time it moves with the person, across systems, sectors, and borders.
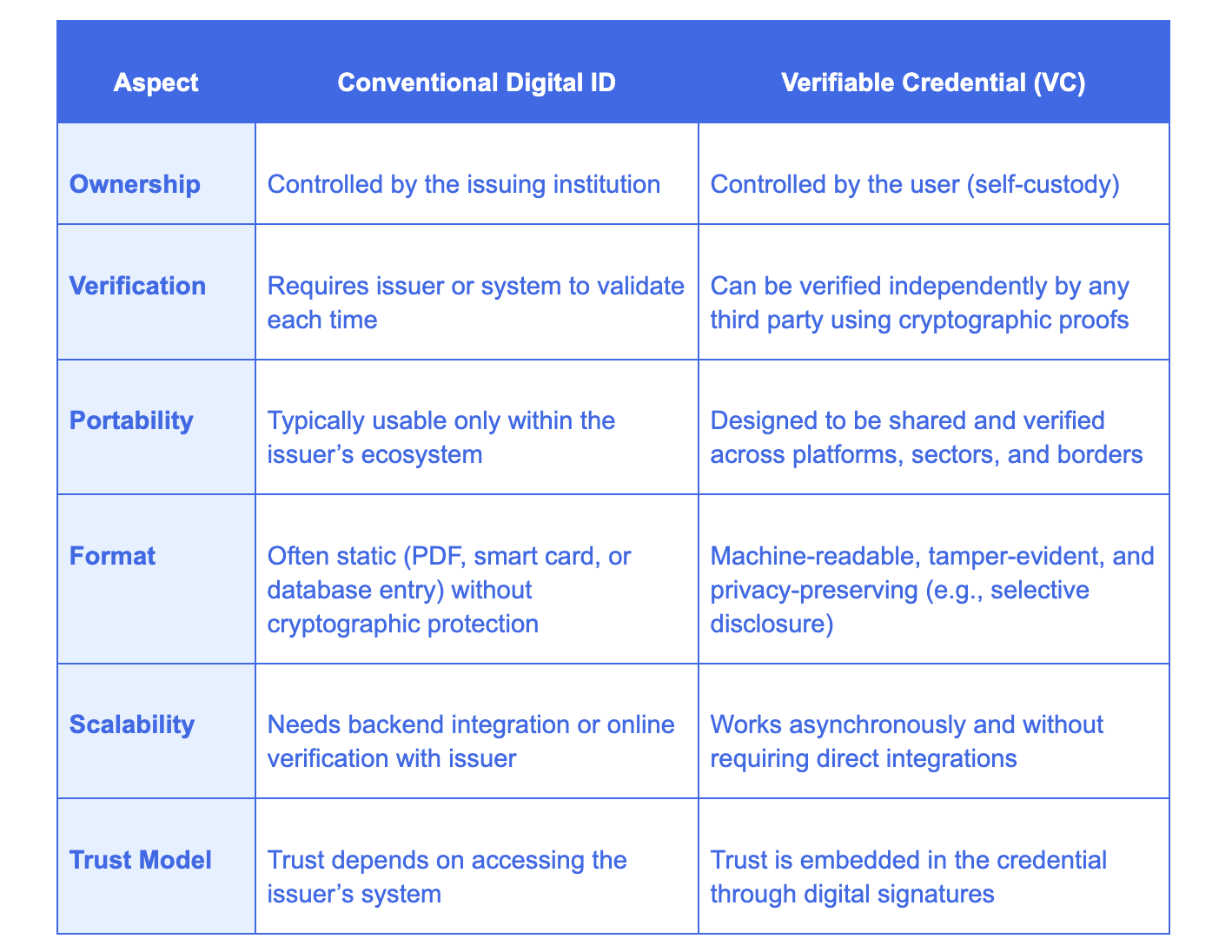
The following table summarizes how VCs compare to conventional digital IDs:
What Changes When People Control Their Own Data?
The shift to VCs changes the trust model entirely. Instead of asking the system to confirm the data each time, the trust travels with the data itself.
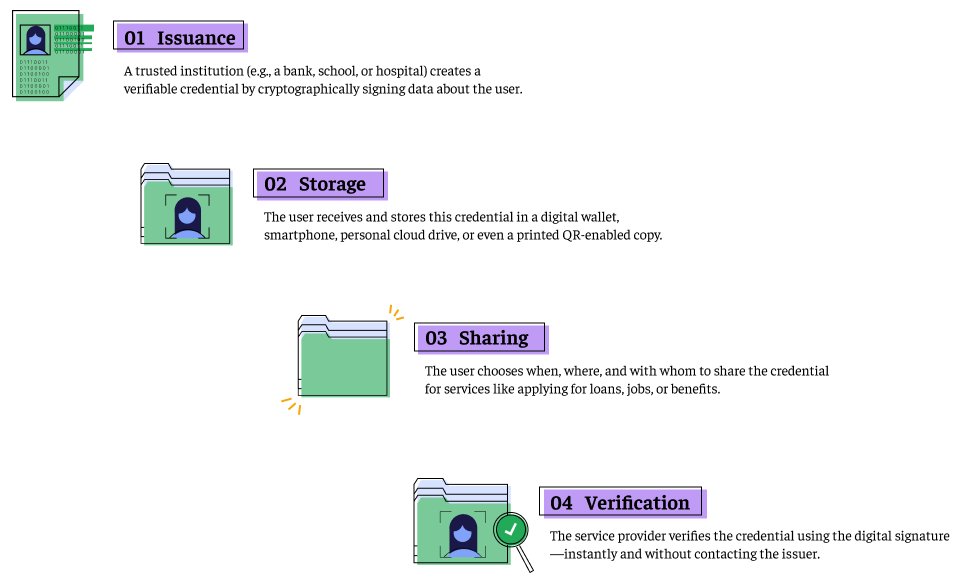
By embedding trust into the data, verifiable credentials unlock faster and more inclusive access to services across sectors, borders and systems.The process may sound technical, but it’s simple in practice. Here’s how a verifiable credential works from issuance to verification and how control stays with the user at every step.
What begins as a technical change quickly becomes a foundation for inclusion and opportunity. And when adopted at scale, the impact reaches far beyond individuals.
So What Happens When This Approach Is Adopted At Scale?
For millions outside formal systems such as informal workers, small traders, and migrant families, VCs offer a way to prove identity, income, or experience without relying on institutions each time. This reduces friction and opens access. For banks, employers, and governments, it removes the need for costly integrations and manual checks. Credentials can be verified instantly, making services like loans, jobs, school admissions, and subsidies faster, simpler, and more inclusive. Since the model does not depend on backend integrations, it works even in low-resource settings and across borders. These are not abstract ideas. They are already being implemented, with practical, scalable results.
Let’s take a look at how.
In finance, small business owners who previously struggled to access credit can now present signed sales logs, tax records, or bank statements issued by trusted entities. These credentials, when shared with a lender, serve as verified proof of income and repayment capacity, eliminating the need for backend system checks or manual document vetting. This shift enables more inclusive lending decisions, especially for entrepreneurs in informal or semi-formal economies. Brazil’s GOV.br platform and Argentina’s Mi Argentina app already support this kind of document sharing at scale (OECD, 2022).
In healthcare and social services, verifiable credentials allow patients to carry a health ID that can unlock a consolidated, accurate record of their past visits, prescriptions, vaccinations, or diagnostic results. Imagine walking into a new clinic and the doctor, with your consent, instantly seeing your full treatment history without calling previous hospitals or asking you to recall past illnesses. This is already possible in countries for instance in Singapore, Singpass enables users to access their medical records, book appointments, and manage health insurance through the HealthHub portal (GovTech Singapore, n.d.).
In education and employment, jobseekers and students can carry verifiable degrees, certificates, and employment letters in a format that can be instantly checked by recruiters or institutions; no need to chase down universities or employers for confirmation. Platforms like Singapore’s OpenCerts and the UK’s Digital Identity and Attributes Trust Framework make these exchanges efficient, fraud-resistant, and user-led. OpenCerts uses blockchain to issue and verify tamper-proof educational certificates (GovTech Singapore, n.d.), while the UK framework sets standards for secure, user-consented digital identity exchanges across sectors (UK Department for Science, Innovation and Technology, 2023).
In the energy sector, verifiable credentials are being used to support green infrastructure programs. For instance, a solar panel owner can present a credential issued by a regulatory body that confirms their energy production eligibility. In the energy sector, verifiable credentials are helping streamline access to green energy subsidies and carbon credit programs. For example, a solar panel owner can receive a digital certificate from an approved regulatory agency confirming how much clean energy they’ve produced. This certificate can then be used to automatically claim government subsidies or participate in Renewable Energy Certificate (REC)5 markets, without waiting for lengthy inspections or manual audits by third-party verifiers.
In governance and identity, verifiable digital IDs act as a foundational layer that allows individuals to access public services, prove eligibility for welfare, and complete cross-border interactions without repeating KYC checks. Unlike domain-specific credentials like tax records or health IDs, digital IDs work across sectors. Hong Kong’s iAM Smart and the UAE’s UAE PASS are moving toward blockchain-enabled, user-controlled IDs that support secure, cross-border verification (OECD, 2023; UAE Digital Government, 2022).
These examples point to the direction our systems are already beginning to take.
From System Portability to User-Led Data Sharing
Verifiable credentials represent a return to something we once had user-held data that was portable, trusted, and easy to share. In the pre-digital era, people carried their own medical files to clinics and presented passbooks at banks. These physical records empowered individuals to manage and share information without needing systems to coordinate or connect (Matthan, 2024).
Today, even though systems are digital, this agency has been lost. Our health records, bank statements, and educational certificates are often locked within institutional silos. Data access is mediated through portals and APIs, and controlled by the issuing institutions. To return more control to the user, jurisdictions have responded with system-led frameworks: the European Union’s General Data Protection Regulation (GDPR) includes the right to data portability, Australia implemented the Consumer Data Right (CDR), and India introduced the Data Empowerment and Protection Architecture (DEPA) to enable consented data flows across regulated systems (Matthan, 2024).
While these efforts represent major progress, they still rely on system-to-system API-based connectivity and aligning the digital infrastructures of multiple organizations; each with different capacities and standards, is time-consuming, costly, and difficult to scale across sectors.
Verifiable credentials offer a more lightweight, user-centric alternative. Rather than waiting for institutions to integrate with each other, each entity can issue cryptographically signed credentials directly to users. These credentials are tamper-evident and independently verifiable, no backend integration or real-time system access required.
This approach benefits both users and institutions. It lowers the operational cost of data verification, reduces dependence on complex API networks, and enhances trust and compliance through cryptographic assurance.
This is the model CDPI advocates: one where credentials are issued once, held by users, and reused across ecosystems to unlock access, portability, and inclusion (Centre for Digital Public Infrastructure, 2025). It enables a shift from institutional data portability to user-held, self-custodial portability, one that is simpler to scale and more equitable in practice.
APIs made data portable for institutions. Verifiable credentials can now make it portable for users.
References
Centre for Digital Public Infrastructure. (2025). Vision paper: User-centric credentialing and personal data sharing (Version 1.0).
https://cdpi.dev
GovTech Singapore. (n.d.). HealthHub – One-stop access to your health records and services.
https://www.healthhub.sg
GovTech Singapore. (n.d.). OpenCerts: A platform for issuing and validating educational certificates.
https://www.opencerts.io
Matthan, R. (2024). Verifiable credentials and the return of user-held data. Paragraph. https://paragraph.com/@exmachina/verifiable-credentials
OECD. (2022). Digital identity for development: Global insights. https://www.oecd.org/digital/digital-identity-development.pdf
OECD. (2023). Technology and digital government: Trusted data infrastructure and services. https://www.oecd.org/gov/digital-government/
OpenID Foundation. (2023). OpenID for verifiable credentials.
https://openid.net
RBI. (2022). Annual report 2021–22. Reserve Bank of India.
https://www.rbi.org.in
UIDAI. (2023). eKYC guidelines and updates. Unique Identification Authority of India.
https://uidai.gov.in
UK Department for Science, Innovation and Technology. (2023). UK digital identity and attributes trust framework. https://www.gov.uk/government/publications/uk-digital-identity-and-attributes-trust-framework
UAE Digital Government. (2022). UAE PASS: The National Digital Identity. https://u.ae/en/about-the-uae/digital-uae/uaepass
Varma, P. (2023). Credentialing for scale: Why verifiable credentials matter for digital identity. Centre for Digital Public Infrastructure. https://cdpi.gitbook.io/user-centric-credentialing-and-personal-data-sharing
W3C. (2022). Verifiable credentials data model v1.1. World Wide Web Consortium. https://www.w3.org/TR/vc-data-model/
World Bank. (2021). World development report 2021: Data for better lives. https://www.worldbank.org/en/publication/wdr2021
World Bank. (2022). Global Findex Database 2021: Financial inclusion, digital payments, resilience, and the gender gap. https://www.worldbank.org/en/publication/globalfindex
Paga is a licensed mobile money operator in Nigeria that allows users to send and receive money, pay bills, and access basic financial services via mobile phones, even without a bank account. It was founded in 2009 to drive financial inclusion.
Opay is a Nigeria-based fintech platform offering mobile payments, banking, and digital services. It supports peer-to-peer transfers, merchant payments, and wallet-based transactions, particularly in underserved markets.
An ajo is a traditional Rotating Savings and Credit Association (ROSCA) practiced in Nigeria, where members contribute a fixed amount regularly and take turns receiving the pooled sum. It serves as a community-based financial safety net and savings mechanism (Bouman, 1995).
Cryptographic techniques refer to methods used to secure data by transforming it into a format that can only be read or verified by someone with the right key. These include encryption, digital signatures, and hashing, which help ensure that information is authentic, confidential, and unaltered.
Renewable Energy Certificates (RECs) are market-based instruments that certify the bearer owns one megawatt-hour (MWh) of electricity generated from a renewable energy resource. RECs are used to track and trade renewable energy and serve as proof of the environmental attributes of green power, enabling compliance with renewable energy mandates or voluntary sustainability goals.